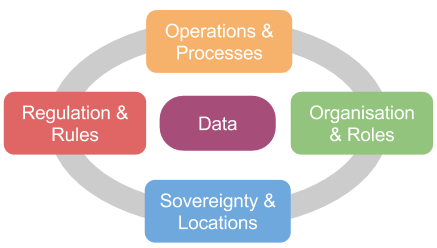
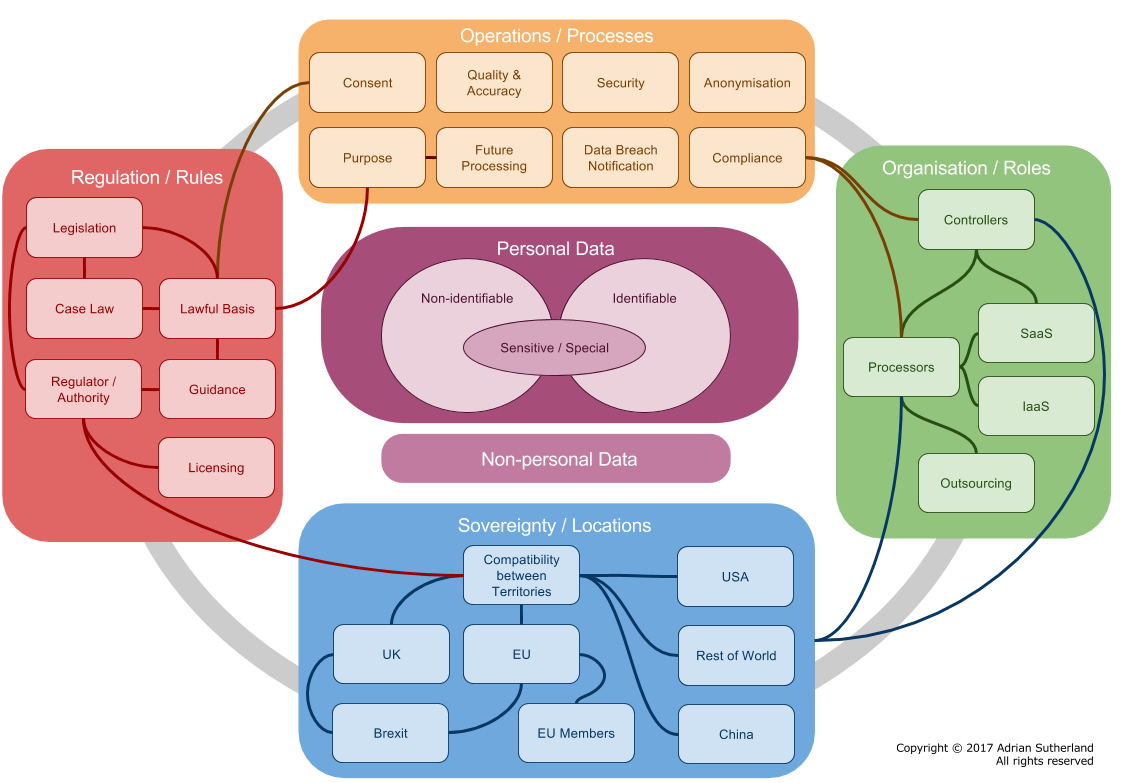
Data Protection and Cloud Computing Framework
This framework is based on the work I have done over several years looking at data protection globally. The point of the framework is to provide a structure to map on country and industry specific regulations and also to provide a simple checklist. Issues of privacy and data protection are of paramount importance when considering cloud computing because in many instances it covers processing of personal data and this poses recurrent issues relating to the applicable law, the determination of roles, contracts required, and the international transfer of data.
This is a living document that I work (sporadically) to expand - but its main purpose is to share a structure for requirements and other regulatory aspects when considering cloud and personal data. Currently I am adding details of the new EU General Data Protection Regulation (GDPR) Regulation - a fundamental step change - and hope this helps understanding of the new legal framework in the EU. I have started by noting major changes (marked with GDPR) rather than revisiting everything - however I accept a re-write will be needed!
Overview
Across the globe Governments are focusing more attention on Cloud computing both for their own computing needs and as a growth sector in their economies - for example in the USA, Australian and Europe. The European Union has shown particular interest in cloud computing in the framework of its digital agenda including a strategy for “Unleashing the Potential of Cloud Computing in Europe”.
Issues of privacy and data protection are of paramount importance when considering cloud computing because in many instances it covers processing of personal data and this poses recurrent issues relating to the applicable law, the determination of roles, contracts required, and the international transfer of data.
Data
Identifiable and Non-Identifiable Data
Personal data generally means data which relate to a living individual who can be identified. There are also often restraints on disclosing non-identifying information, including the publication of general and aggregate data.
It is important to note that the ability to identify an individual can include scenarios where other information / actors are needed to identify the person - this therefore often makes "anonymous" data identifiable. For example, where age and address from one dataset can be combined with a voters register to match individuals - in this case both datasets are Identifiable data. Globally, pseudonymised, and even anonymised data, is becoming considered to be identifiable personal data, for these same reasons.
Sensitive / Special Data
Sensitive data generally means such data as: ethnic origin, political views, religion, trade union membership, health, sexual life, criminality or criminal proceedings. This data typically has tighter rules associated with it.
Financial data is also treated specially with regards to security for example.
Non-Personal Data
Not all data regulations concern Personal Data - there are also barriers to the movement of non-personal data including data localisation restrictions, legal uncertainty on cross-border data processing, concerns of data availability for regulatory purposes, and lock-in to service providers. So, for example, the EU Commission is proposing a regulation aimed at removing obstacles to the free movement of non-personal data.
Regulations
Lawful Basis
Generally the key principle is that is there is not a lawful basis to processing personal data then that processing is unlawful - the new EU General Data Protection Regulation (GDPR) is perhaps the clearest codification of this general principle. Lawful basis typically covers: consent, performance of a contract with the data subject, legal obligation, vital interests, or the public interest.
Regulator & Guidelines
EU Guidance
The EU ‘Article 29 Working Party’ (Working Party) has issued numerous opinions which are relevant to cloud computing, including:
- Opinion 05/2014 on anonymisation techniques
- Opinion 03/2014 on personal data breach notification
- Opinion 03/2013 on purpose limitation
- Opinion 15/2011 on consent
- Opinion 8/2010 on applicable law
- Opinion 4/2007 on the concept of personal data
The Working Party published an opinion dedicated to cloud computing, Opinion 05/2012 which analyses all relevant issues for cloud computing service providers (“CSP”) operating in the European Economic Area, and their clients, specifying all applicable principles from the EU Data Protection and ePrivacy Directives.
National Guidance
Most local data protection authorities (“DPA”) have issued data protection guidance dedicated to cloud computing.
- A few have not including Belgium, Denmark (there are however cloud–specific decisions of the Danish DPA), Finland and Poland.
- Countries that have issued general guidance on cloud computing all cover data protection aspects (e.g., Belgium and Denmark).
The absence of dedicated guidance on data protection in a cloud environment does not mean that other guidance published by local DPA’s on more general topics does not apply. In general, national guidance does not provide divergent views from the ones set out in the EU Guidance.
Legislation & Case Law
Legislation is the formal laws create by national and supranational Governments, case law is created by judges by their judgements on cases.
Several decisions of the Court of Justice of the European Union (CJEU) are worth taken into account. Judgments of the CJEU apply throughout the EU.
- Referring to persons on an Internet page constitutes processing of personal data.
- An Internet search engine operator is responsible for the processing that it carries out of personal information.
- The processing and storage of data relating to Union citizens for statistical purposes or with a view to fighting crime is contrary to Community law.
Case law in the United States
One of the areas of key concern is the interplay between EU data protection rules and laws in other countries that seemingly conflict. Given the US origin of many of the largest cloud vendors, the size of the US market and revelations about NSA surveillance and information gathering, the position in the US continues to be watched closely.
In the Microsoft Warrants case, it was found that Microsoft must comply with a warrant to disclose records in a particular MSN email account and that the location of the data (in Dublin) was not relevant because Microsoft still “controlled it”. Microsoft decided not to comply with the order, voluntarily putting itself in contempt, and is continuing to seek ways to appeal the decision. Apple, Cisco, Verizon and AT&T all filed Amicus briefs in support of Microsoft’s appeal on the basis that finding in favour of the US Government would conflict directly with EU data protection laws. The case will continue but what is certain is that the lack of clarity and the potential conflicts of laws present real challenges for US cloud vendors and their customers. Update - This case is now before the US Supreme Court.
Licensing
The outsourcing of the hosting of certain data is specifically regulated under the national laws of some countries. Examples, for health data, are:
- France. A hosting service provider must be approved by the Shared Healthcare Information Systems Agency.
- Finland. Entities providing healthcare services are responsible for compliance even when they decide to outsource the processing. Processors need to pay attention to the recent regulation on electronic processing of personal health data; they need to fulfil specified requirements of interoperability, data security, data protection and other functionality.
- Poland. The Inspector General for the Protection of Personal Data view is that IT outsourcing in the medical sector is not allowed due to lack of clear legal provisions with regard to disclosure of medical secrecy. The Ministry of Health is conducting a public consultation on this subject.
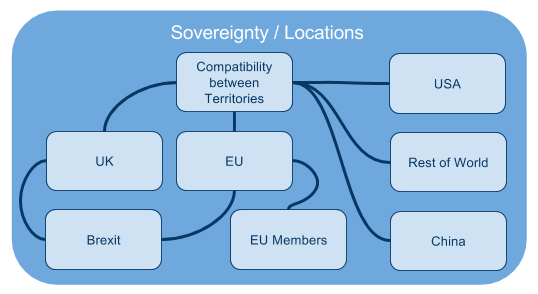
Location
One of the areas of key concern is the interplay between EU data protection rules and laws in other countries that seemingly conflict. Given the US origin of many of the largest cloud vendors, the size of the US market and revelations about NSA surveillance and information gathering, the position in the US continues to be watched closely.
In the Microsoft Warrants case, it was found that Microsoft must comply with a US warrant to disclose data in Dublin because Microsoft still “controlled it”. Microsoft decided not to comply and voluntarily put itself in contempt. The case will continue but what is certain is that the lack of clarity and the potential conflicts of laws present real challenges for US cloud vendors.
GDPR imposes restrictions on the transfer of personal data outside the EU - conditions for transfer set out in Chapter V.
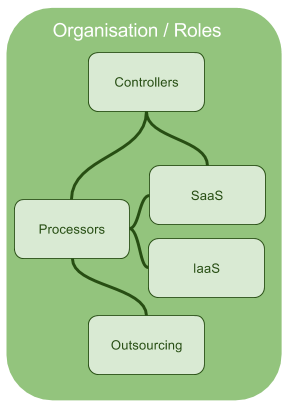
Organisation
Controllers and Processors
In short, the controller says how and why personal data is processed and the processor acts on the controller’s behalf.
GDPR places specific new legal obligations on processors; for example, the requirement to maintain records of personal data and processing activities, and add significantly legal liability for a breach. The controller is not relieved of obligations where a processor is involved – the GDPR places further obligations to ensure contracts with processors comply with the GDPR.
Cloud Computing - IaaS, IaaS and Outsourcing Generally
International ISO standards
Standards serve as an increasingly important tool for cloud customers to determine whether a cloud computing solution is secure and reliable.
Until recently CSPs could only rely on general certification schemes. However, a cloud-specific voluntary certification scheme saw the light of day in July 2014, with the publication of ISO/IEC 27018. This code of practice is based on the 2012 European Cloud Computing Strategy and the Working Party’s Opinion 05/2012 on Cloud Computing. Its objectives are to function as a compliance tool for data protection obligations, to provide a more transparent cloud service, to assist contract negotiation, and to provide audit mechanisms.
More recently, ISO/IEC 17788 and 17789 were adopted providing for a common terminology and architectural framework.
EU guidance
The European Network and Information Security Agency has published reports on security in a cloud-computing environment. In particular the following areas have been covered:
- Information security benefits and key security risks of cloud computing with practical recommendations.
- Assurance criteria designed to assess the risk of adopting cloud services and to compare CSP offerings.
- A decision-making model to determine how operational, legal and information security requirements can drive the identification of the architectural solution that best suits the needs.
- Monitoring of security.
- Identification of the Member States with government Cloud infrastructures.
- Incident reporting schemes.
- Critical Information Infrastructure Protection (includes a number of relevant scenarios and threats).
The Working Party Opinion 05/2012 on Cloud highlights the fact that “in addition to the core security objectives of availability, confidentiality and integrity, attention must also be drawn to the complementary data protection goals of transparency, isolation, intervenability, accountability and portability”. The opinion analyses such questions more in depth.
National guidance
In Germany, the guidance paper “Orientierungshilfe Cloud Computing” (updated version 2.0 of 9 October 2014) of the German data protection authorities contains comprehensive recommendations on cloud computing, including rules on security which are similar to those in the Working Party Opinion 05/2012.
The guidance of the German Federal Agency for Security in Information Technology entitled “Security Recommendations for Cloud Computing Providers” deals with IT security related topics, such as security management; architecture; rights management; options for users; monitoring and security incident management; business continuity; portability and interoperability; security testing and audit; requirements on personnel; agreements; data protection. The paper includes different levels of (security) requirements depending on the sensitivity of data stored in the cloud: Category B (basic requirement), Category C+ (additional high confidentiality requirements), and Category A+ (additional high availability requirements).
In Spain, there is no explicit guidance on security in the cloud but this is covered in cloud-related guides from the DPA and the “Guide for companies: security and privacy of Cloud computing” published by the Ministry of Industry, which examines the main implications as regards security and privacy, and in particular covering security in the cloud.
Process
Security
Security is currently one of the most regulated topics in the field of data protection and the importance given to security is constantly increasing.
The EU requires that the controller guarantees the security of the personal data and protects their integrity. In order to do so, the controller (or its processor) must implement the ‘appropriate’ technical and organizational measures “in particular where the processing involves the transmission of data over a network”.
The EU provisions are formulated in general terms. Member States have a relatively high level of discretion when implementing these and have taken different approaches. Some of them have transposed the EU provisions faithfully (e.g. The United Kingdom) others are more prescriptive (e.g. Poland, Germany and Spain). Practical guidelines on how to implement the, often vague, legal provisions has been published by the European Network and Information Security Agency and national guidance has been published in Belgium, Germany, Poland, and Spain.
Until recently CSPs could only rely on general standards certification schemes. However, a cloud-specific voluntary certification (ISO/IEC 27018) was published in 2014. This code of practice is based on the 2012 European Cloud Computing Strategy and the Working Party’s Opinion on Cloud Computing.
The Working Party Opinion on Cloud highlights the fact that “in addition to the core security objectives of availability, confidentiality and integrity, attention must also be drawn to the complementary data protection goals of transparency, isolation, intervenability, accountability and portability”.
Anonymisation
The need to take into account issues relating to privacy and the processing of personal data made it only natural for the growing interest in techniques that would allow eliminating or at least mitigating the risks related to the processing of such data.
Data protection applies to any information concerning an identifiable person but not to data where the person is not identifiable.
The Working Party considers that equating pseudonymisation to anonymisation is one of the misconceptions among many data controllers. This is because pseudonymised data still allows an individual data subject to be singled out and linkable across different data sets, hence in most instances pseudonymised data remains subject to data protection rules.
According to the Working Party, once data is truly anonymised and individuals are no longer identifiable, EU data protection rules no longer apply.
A factor that needs to be considered is whether there is any kind of other data that could be used to identify the individual. For example, if a data controller keeps the original (identifiable) data, and hands over part of this dataset by removing the identifiable data to another party; the resulting dataset will still constitute personal data.
Overall, the Working Party seems to imply that a true anonymisation might not be achievable in a world of “open” datasets; indicating that given the current state of technology and the increase in computational power and tools available, identification is easily attainable. Such an approach will significantly affect the widespread use of cloud services.
In Italy and Spain the DPA’s have made decisions covering data anonymisation.
In the United Kingdom, a Code of Practice explains how to balance the privacy rights of individuals while providing rich sources of data. It takes a different view than the Working Party, the view in the UK is that where information is anonymous in the hands of the recipients, it will not be considered to be personal data in the hands of those recipients, even if the original controller retains the ability to re-identity that data.
GDPR Update. The use of anonymisation and pseudonymisation to produce non-identifiable or non-personal data hinge on their abilities to protect data subjects from re-identification, and in my view the assumption must be that re-identification is entirely feasible in most cases.
Data-breach Notification
In spite of the absence of a general EU rules applicable to all organisations, breach notification is gradually becoming the norm in the EU. The General Data Protection Regulation will in all likelihood introduce a general data breach notification obligation. Furthermore, the draft Cybersecurity Directive also provides for breach notification in the framework of network and information.
The Working Party proposes a list of scenarios where data subjects should be notified. National notification regimes exist in Germany, Belgium, the United Kingdom, and Italy.
GDPR update - A notifiable breach has to be reported to the relevant supervisory authority within 72 hours of the organisation becoming aware of it - possibly in phases. If the breach is sufficiently serious to warrant notification to the public, the organisation responsible must do so without undue delay.
Consent
For sensitive data (like health information), in order for consent to be valid, it must be unambiguous; freely given; specific; and informed. For example, in the case where patients refusing an e-health system have to pay a substantial extra cost or that the processing of their file is considerably delayed consent will not have been freely given. Consent in the context of sensitive data must be explicit; the Working Party view is that opt-out solutions will not be sufficient.
The Working Party is of the opinion that such explicit consent does not have to be written, however there are some discrepancies between the Member States.
- In Finland express consent should usually be given in writing.
- In Poland, the consent for sensitive data processing shall be explicit and in written (hard copy) form in order to be valid.
- In France, courts have considered that explicit consent is necessarily provided in writing in order to be valid. However the French DPA may adopt flexible positions; for instance, in the healthcare sector, the French DPA has deemed valid a consent provided through ticking a box at the bottom of a digital form.
Consent under the GDPR must be a freely given, specific, informed and unambiguous indication of the individual’s wishes. There must be some form of clear affirmative action.
GDPR enhances the protection of children’s personal data.
- you must ensure that your privacy notice is written in a clear, plain way that a child will understand
- you may need to obtain consent from a parent or guardian to process the child’s data.
Note: Parental/guardian consent is not required where the processing is related to preventative or counselling services offered directly to a child
Rights
GDPR strengthens and creates some new rights for individuals
- The right to be informed - ‘fair processing information’, typically through a privacy notice - transparency
- The right of access - confirmation that their data is being processed and access to their personal data
- The right to rectification - correct inaccurate or incomplete data, with implications if it has been shared with 3rd parties
- The right to erasure - ‘the right to be forgotten’ where there is no compelling reason for its continued processing
- The right to restrict processing - ‘block’ or suppress processing of personal data
- The right to data portability - obtain and reuse their personal data for their own purposes across different services
- The right to object - right to object to processing (and rules relating to when you may or may not comply)
- Rights in relation to automated decision making and profiling - where automatic processing has a legal or significant effect, individuals must be able to obtain human intervention; express their point of view; and obtain an explanation of the decision and challenge it.
Compliance
Under GDPR you must
- Implement appropriate technical and organisational measures that ensure and demonstrate that you comply. This may include internal data protection policies such as staff training, internal audits of processing activities, and reviews of internal HR policies.
- Maintain relevant documentation on processing activities.
- Where appropriate, appoint a data protection officer.
- Implement measures that meet the principles of data protection by design and data protection by default, e.g. Data minimisation; Pseudonymisation; Transparency; Allowing individuals to monitor processing; and Creating and improving security features on an ongoing basis.
- Use data protection impact assessments where appropriate.
Poster
For those who like it all on one page.
Data Protection and Cloud Computing Framework